TL;DR:
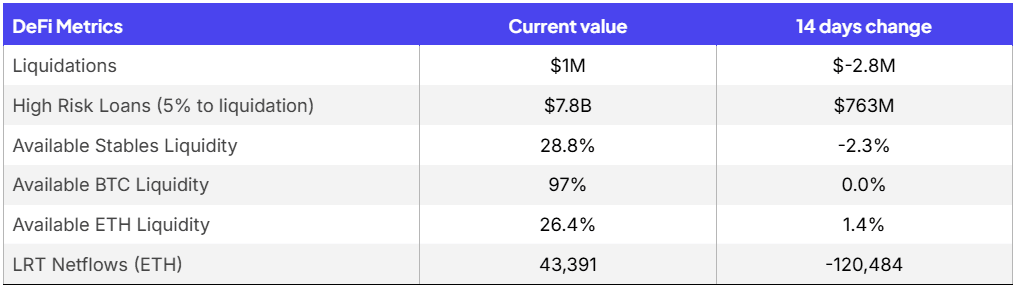
Available liquidity remains high, indication hesitation to take leverage in turbulent market
Liquidations have dropped to $1M over the holidays
Exploit Vector Trends
Changes in liquidity have remained fairly flat as markets stay quiet over holidays
Featured Product: Sentora’s Strategy Portal
Risk Pulse and Radar Highlights
Sentora Risk Pulse
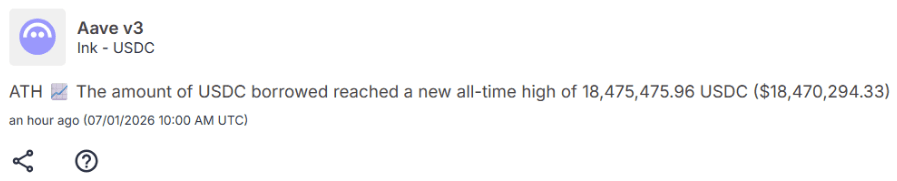
Tydro (Ink’s Aave v3) instance has growing traction
USDC borrow have been continuing to grow with new ATH borrows
Existing USDC borrowers will want to track if this is pushing up the utilization ratio which will increase borrows rates
Sentora Risk Pulse
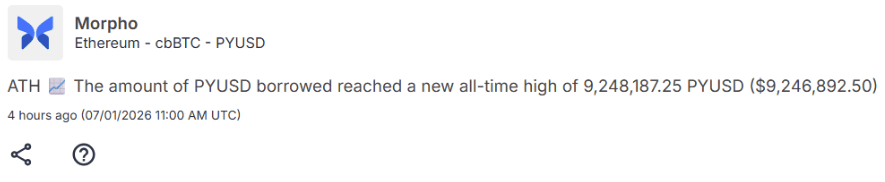
PYUSD is gaining traction on Morpho
Alerts from pulse can identify quickly new markets allowing users to find optimal borrow rates, especially if they are indifferent among stablecoins
Current Event Risks
Exploit Trends Moving Away from Smart Contracts
Smart contract auditing and best practices have been improving in leaps and bounds over the past several years. Additionally, newer Layer 1 blockchains have adopted newer smart contract languages like rust and move that are seen as more resilient from a security perspective than languages like solidity. This evolution has meant the portion of exploits that are tied to smart contract bugs has been shrinking. While this is a positive sign of the DeFi ecosystem maturing, hackers have moved onto other attack channels.
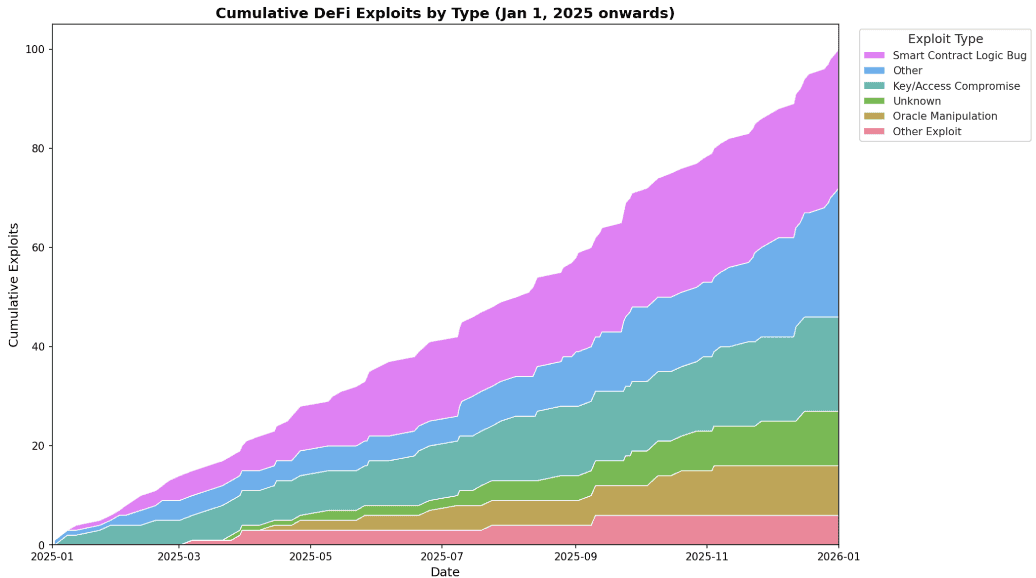
Source: Sentora Research and DefiLlama
Key management has become an increasingly large proportion of exploits
This signals that hackers are turning to social engineering and other methods to attack projects from traditional technology attack vectors instead of through smart contracts
The silver-lining here is that it is becoming harder to exploit smart contracts and higher operational security standards could begin to limit many attack vectors
Feature Dashboard: Strategy Discovery Portal
While Sentora has grown significantly as a vault curator, most of our work centers on institutional partners with specific strategy design, risk constraints, and reporting requirements through our Smart Yields platform. Sophisticated yield activity increasingly happens behind the scenes, bespoke allocations, gated strategies, curated vaults, creating a market where strategy information is unevenly distributed and discovery is largely relationship-driven. DeFi runs on transparent rails, but strategy execution remains opaque: when allocators only see headline APY, the real questions go unanswered. Strategy Discovery aims to change that by reducing information asymmetry and encouraging competition on risk-adjusted yield rather than marketing-driven yield.
Explore Strategy Discovery: portal.sentora.com/discover
What Strategy Discovery shows
Strategy overview built for comparison: Each strategy displays estimated APY, capacity, TVL, strategy type, blockchains, assets, and protocols.
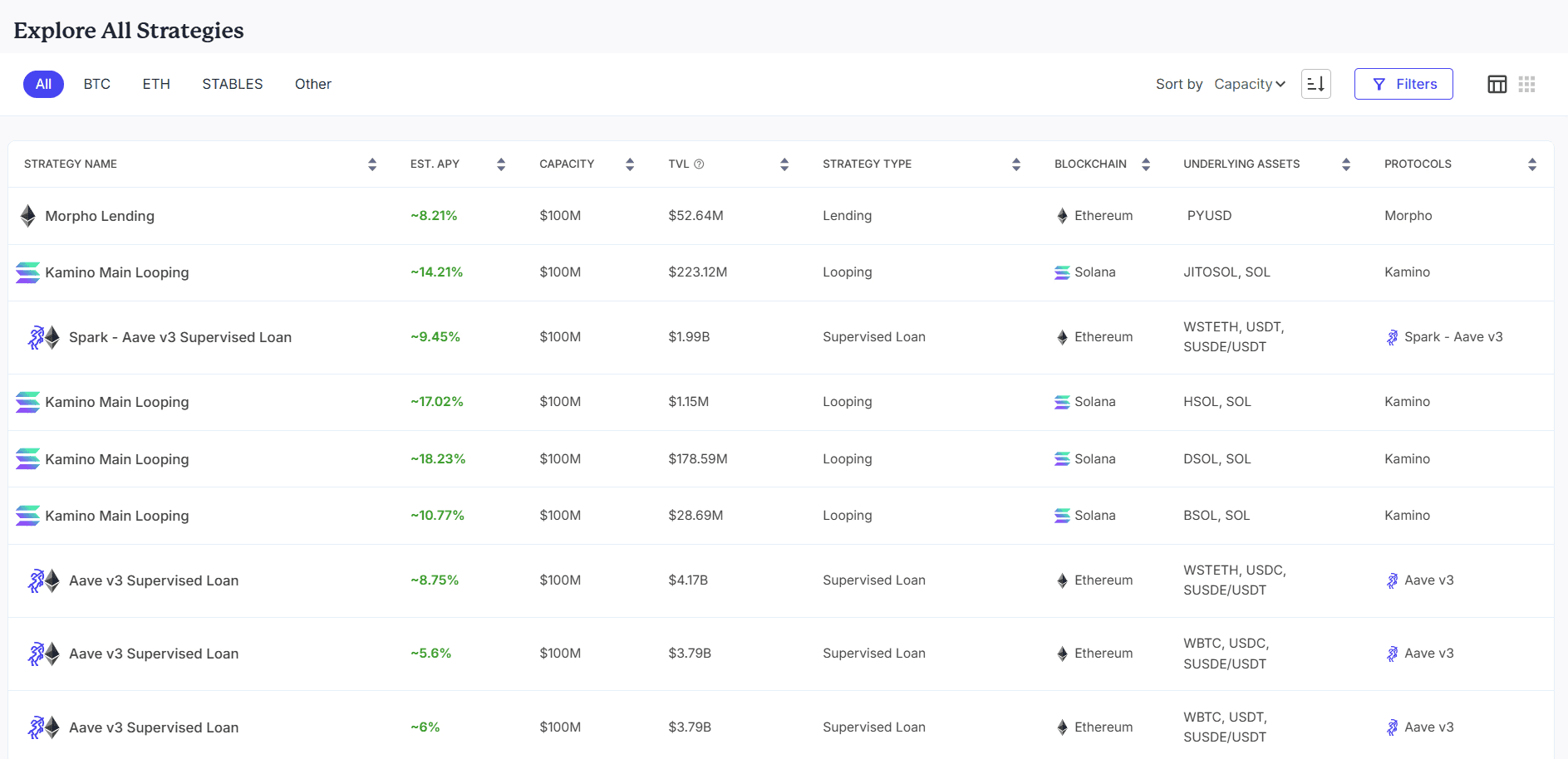
Sentora Strategy Discovery
Strategy pages with analytics: Individual strategies show historical APY, historical capacity, and concise descriptions pairing performance with operational reality.
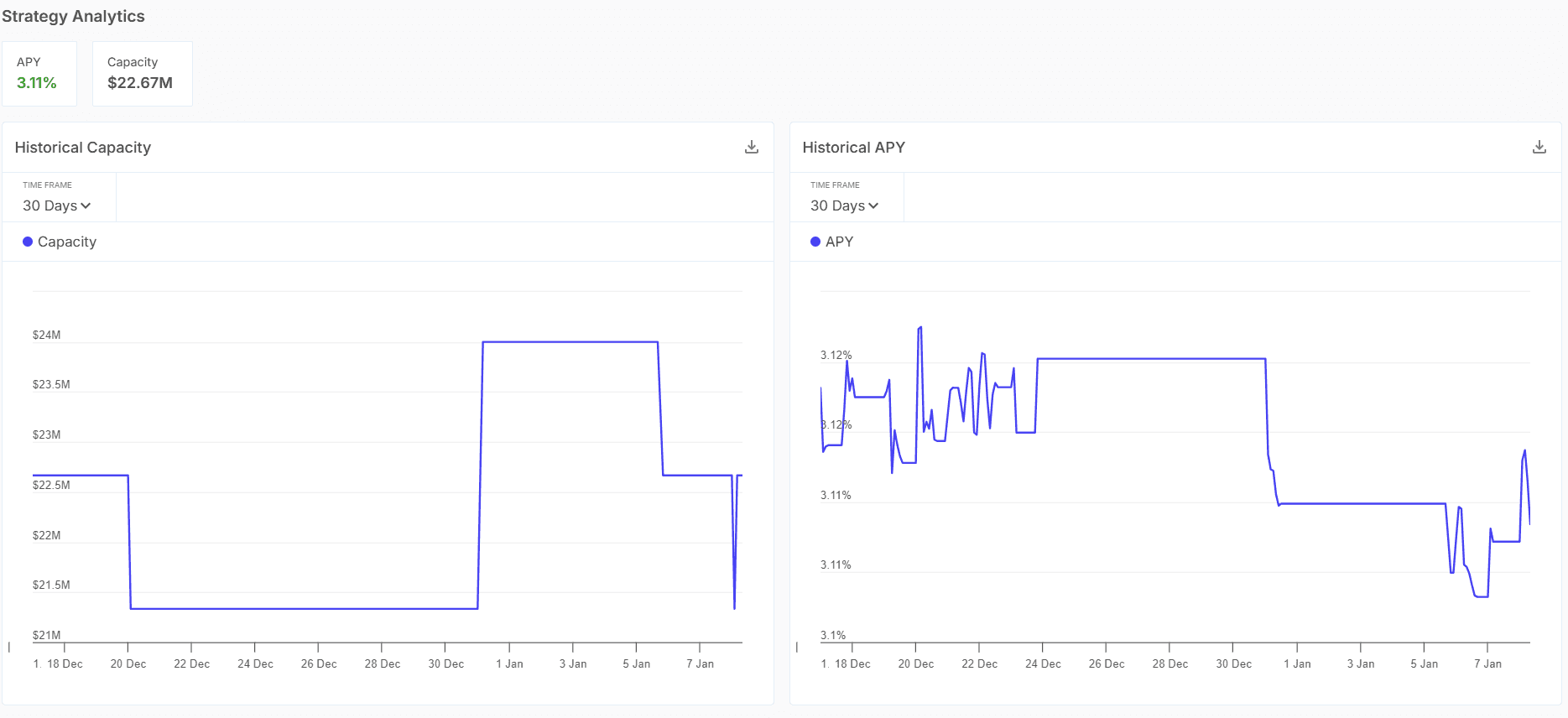
Sentora Strategy Discovery
Note: To access these strategies you need to be a Sentora client
Stay informed, manage risks wisely, and stay liquid
Disclaimer: This newsletter is for informational purposes only and should not be considered financial advice.
EXPLORE MORE ARTICLES


